HIPAA Security Rule
Victim organizations have been paying the demanded ransom in order to get back into normal operations. Health organizations which have experienced a breach or had a non-compliance violation resulting from an audit, face a long way to recovery. The table below highlights the types of violations and associated penalties:. This site is also known as the Wall of Shame. HIPAA requires organizations implement policies and procedures to prevent, detect, contain, and correct security violations.
In this process, a scan of SSH authorized keys can also be proceeded to confirm deployment. Implementing proper policies for defining roles and granting access is critical for compliance with the law. All methods must be considered, including those using key-based credentials. Be ready for when the OCR comes knocking.
Contact UNC
Make sure to implement security measures beyond what the law states since ePHI has become the hottest item in cybercrime. Boost staff members security awareness to prevent and detect breaches. Invest in security tools that help you reduce and even eliminate the risk of ePHI being compromised. Some functionality on this site will not work wihtout Javascript. We recommend you enable Javascript for this site.
Your browser does not allow storing cookies. We recommend enabling them.
COM uses cookies to give you the best experience and most relevant marketing. Some functionality on this site will not work without cookies and our advertising will be less relevant! Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information.
HIPAA Security Rule - What It Means and What to Do?
The requirement of segregation of duties applies to any kind of access, including access using SSH keys. We frequently see key-based access from test and development systems into production, which violates segregation of duties. Implement policies and procedures for authorizing access to electronic protected health information.
Implement identity and access management. Assess and manage SSH key based access. Ensure that tunneled access from the public Internet to intranet is not possible. Coverage of individual health information is also very similar. Both the HIPAA Security Rule and the Privacy Rule cover information created by these parties that can individually identify a patient, but the Security Rule applies only to the information that is electronically transmitted, not information that is transmitted orally or in writing.
HIPAA Security Rule | HIPPA Compliance | HIPAA
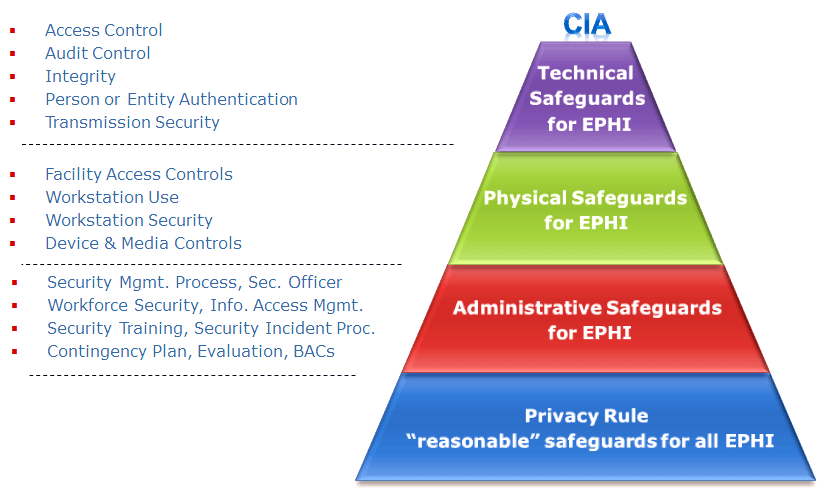
In order to properly manage all risks to security and breaches of information, the Security Rule has mandated that all covered entities follow security guidelines to keep their practices in check. One of the most important risk management practices is a Risk Analysis, an on-going record review process that tracks access to electronically stored information, detects security incidents, evaluates potential risk points, and assesses security measures put into place. These safeguards cover administrative, technical, and physical practices to ensure complete compliance.
Some deal directly with the personnel in a healthcare environment and range from designating a security official responsible for overseeing security procedures, providing supervision and authorization requirements for those working with electronic information, training all employees to be compliant with the Rule and understand the guidelines established at the practice, and performing periodic assessments of the security and privacy practices being implemented. Just as with the Privacy Rule, the Department of Health and Human Services provides education, training, and some technical assistance to help all covered entities stay within the guidelines set forth by the Security Rule.
Security Rule Goal: Protect Digital Patient Information
One of the biggest obstacles that healthcare organizations are trying to overcome today is just how easy it is to breach private information. If a violation is reported, the Department of Health and Human Services, along with the Office of Civil Rights, has the authority to impose civil or criminal penalties. However, fines cannot be imposed under some circumstances, such as if a health care professional unwillingly violated the Rule and if it was committed under reasonable circumstances.
Covered entities are also given up to 30 days to rectify the violation from the time of the act before these fines can be imposed. Criminal penalties can also be enforced and include monetary fines and imprisonment for a number of different degrees of violation.